Passwords and Security Information
How does ADAM store passwords?
ADAM stores passwords in its database using a one-way salted hash algorithm.
- Because it is a one-way algorithm, it is not possible to determine what your original password was.
- Because it is “salted”, even if two or more people do have the same password, someone looking at the database would see different hash values and not know.
How can you tell if I give you the right password?
Very simply, we perform the same algorithm on the password you provide when you log in to the system and see if we end up with the same hash. If they match, then you must have provided the correct password. If they don’t, then you gave an incorrect password.
As an analogy: how could you tell if someone used the same ingredients to make two different cakes? Once the cakes are baked (baking is the one-way operation in this scenario), you can’t see the ingredients any more. However, a skillful taster will be able to compare the flavours of the two cakes to see if they taste exactly the same.
Is my password ever written down or stored anywhere?
Never in anything that could be considered permanent storage.
To be clear, when you type in your password, your computer encrypts the login request and sends that to the ADAM server which decrypts it into memory. The password is then checked against your account (see one-way hashing above) for validity and, if it hasn’t already been checked before, ADAM will check your password against the haveibeenpwned.com password service which checks passwords against a database of known breached passwords.
If you are technically minded, you can read the technical details of how we manage this without compromising your password security.
In the process of checking your password, ADAM stores a SHA-1 hash of your password in the database until such time as the password is checked. SHA-1 hashing is a common, secure, but unsalted mechanism of one-way hashing a password. This hash is required by the haveibeenpwned.com service and is used solely for that reason. The checks happen every 5 minutes. The storage space is located entirely in temporary memory and is not written to disk. The data for password checks is not backed up.
ADAM tells me there is a problem with my password. Why?
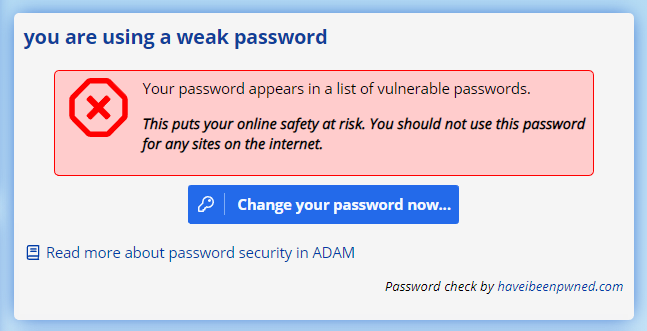
When you log in to ADAM with a new password, ADAM will check your password against the haveibeenpwned.com database of over 500 million compromised passwords. If it discovers that the password has been used before, it records how many times it has been used. We’re hoping it isn’t there at all!
When you visit your landing page, if the password has been used before, ADAM will display a warning similar to this one:
I login to ADAM with my network password. Must I still change it?
Yes!
The fact remains that if you’ve chosen a weak password, that password may make it easier for hackers to compromise the security of the ADAM database by simply logging in with your details and getting access to everything that you can see.
Some schools have ADAM login by quering the password with their network server instead of having ADAM manage a separate password for them. In these instances, ADAM will still check the quality of your password but it can’t give you the opportunity to change it.
In these instances, you should update your network password. When you next log in to ADAM, your new password will be checked.